Each company in the Infocom Group implements systems to protect information assets from unauthorized access, leakage, and other various threats from internal and external sources, clearly identifying mandatory rules. These measures, defined in our Information Security Management Rules, are designed to prevent information security issues. In the event an information security issue arises, these measures work to minimize damages and restore operations as quickly as possible, limiting any loss of confidence by society in our organization.
- The Infocom Group recognizes the importance of information security, conducting security management on a proper and ongoing basis.
- The Infocom Group prioritizes information security over the pursuit of convenience in our business operations.
- The Infocom Group strives to adopt the latest technologies related to information security. However, our decisions reflect a balance based on our assessments of risks involved.
- The Infocom Group requires individuals using group information assets to understand and comply with these rules to ensure high levels of information security.
- We require individuals using group information assets to report immediately to their superior in the event of an information security issue. Such issues must be resolved and measures implemented to prevent recurrence before any other business operations are allowed to continue.
- The Infocom Group complies consistently and conscientiously with all laws and regulations. We provide any training and education necessary to ensure compliance.
We strive to improve the safety and reliability of our information assets and our information security structure. We do so through an ongoing security management process consisting of security planning, security management operations, and security audits.
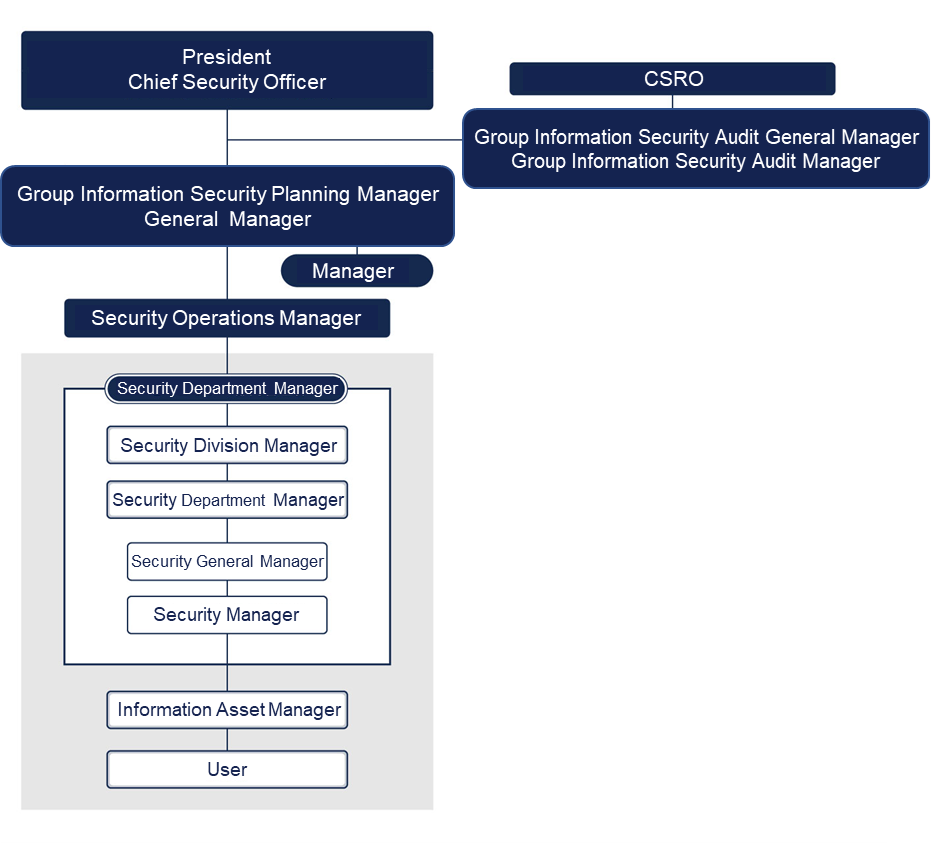
The Infocom Group places the utmost priority on managing and protecting the information of our customers, personal and otherwise. To this end, we maintain and strengthen information security literacy through an organization specializing in information security, while our audit department conducts operational audits. We have also undergo third-party audits to maintain Privacy Mark certification. These and other measures reflect our serious attitude toward information security management.

